A firewall is a computer network security system that restricts internet traffic in to, out of, or within a private network.
By selectively blocking or allowing data packets, this software, or dedicated hardware-software device, functions its purpose. Its primary goal is to deter malicious behaviour and prevent anyone, inside or outside of a private network, from engaging unauthorised web activities.
What is Firewall?
In a private network, firewalls operate as gated borders or gateways that manage the travel of permitted and unauthorized web activity. The term refers to physical barriers that act as barriers against the spread of fire until emergency services workers can put it out. Web traffic management firewalls, in contrast, are often used to restrict the spread of web-based threats.
Firewalls provide “choke points” to direct web traffic, where it is reviewed based on a set of predetermined parameters and handled appropriately. In audit logs, some firewalls also keep track of connections and traffic to show what has been allowed or banned.
Typically, a private network’s or its host devices’ borders are protected by a firewall. Firewalls are a security tool in the broader user access control category as a result. These barriers are often set up between two specialised network computers or user computers and other endpoints (hosts) themselves.
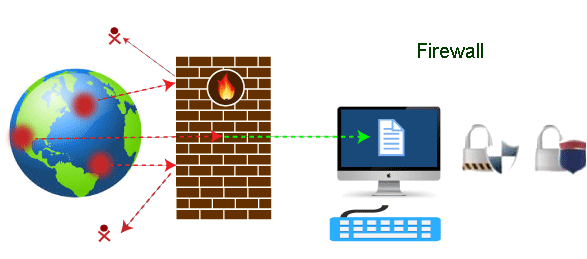
How do firewalls work?
A firewall is just a type of router or computer with two network interface cards that filters incoming network packets in its most basic form. This device is often referred to as a packet-filtering router.
The router determines whether to forward the packets to their intended destinations or to stop them by comparing the source addresses of these packets with an access list specifying the security policy of the firewall.
The IP address or domain name from which the packet originated can be used by the firewall to swiftly determine whether it should allow or ban the traffic. However, access to networks cannot be granted or denied using packet-filtering routers based on a user’s credentials.
Additionally, packet-filtering routers can be set up to allow some types of traffic while blocking others. On the firewall system, this is often accomplished by enabling or disabling different TCP/IP ports. While other ports (like port 23 for Telnet) may be disabled to prevent Internet users from accessing other services on corporate network servers, port 25 is typically left open to permit Simple Mail Transfer Protocol (SMTP) mail to travel between the private corporate network and the Internet.

Firewall allowing Good Traffic
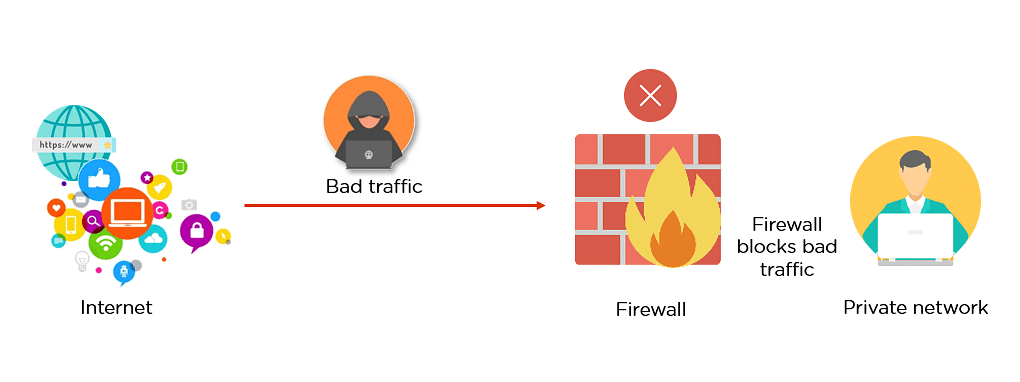
Firewall blocking Bad Traffic
The problem with this approach is that if multiple domains or ports are blocked and many exceptions have been configured, the size of the access list for the firewall can grow significantly. The numbers of ports for some services are assigned at random (such as remote procedure call services) on startup; it is more difficult to configure firewalls to control access to these ports.
Network-level firewall
Network firewalls are made to restrict the transmission of data between networks. They are often employed between a private network with strong security and another network, like the Internet. A secure private network can also be equipped with network firewalls to reduce the risk of cyberattacks and stop unauthorised access to sensitive information.
Network firewalls analyse both incoming and outgoing network traffic, looking for IP addresses, communication protocols, content types, and other aspects of the traffic. The network firewall decides whether to block or let traffic based on specified firewall rules after analysing the traffic’s characteristics.
To comply with security, privacy, and compliance regulations like the Federal Information Security Modernization Act (FISMA) in the United States and the widely accepted Payment Card Industry Data Security Standard (PCI DSS), network firewall security is frequently necessary.
Circuit-level Gateway
Another simplified type of firewall is a “circuit-level gateway,” which can be easily configured to allow or block traffic without using a lot of processing resources. By confirming TCP (Transmission Control Protocol) connections and sessions, these types of firewalls typically function at the OSI model’s session-level. Circuit-level gates are designed to ensure the security of the established sessions.
Circuit-level firewalls usually come as pre-existing firewalls or security software. These firewalls analyse information about transactions but do not check for actual data, which is similar to packet-filtering firewalls. Therefore, if a piece of data has malware in it but uses a correct TCP connection, the gateway will let it through. Circuit-level gateways are therefore not seen to be secure enough to safeguard our systems.
Application-level firewall
Proxy firewalls operate as a middle device to filter incoming traffic between two end systems (such as network and traffic systems) at the application layer. These firewalls are referred to as “Application-level Gateways” for this reason.
These firewalls transfer requests from clients pretending to be original clients on the web server, in contrast with usual firewalls. By protecting the client’s identity and any other potentially dangerous information, the network stays safe from potential attacks. The proxy firewall examines data packets coming from the source after the connection is made. The proxy firewall transfers an incoming data packet to the client if its contents are safe. This method creates an extra layer of security between the client and a wide range of network sources.
Configuring a firewall with packet-filtering
The most basic way to set up a packet-filtering firewall is to initially block all packets and then, case-by-case, start allowing access to the internal network. Avoid saving sensitive information on a machine that is carrying out the firewall software itself and make sure that internal network addresses are not transmitted over the firewall to the outside world. Consider your firewall machine to be expendable; the worst-case scenario should be damage to the firewall triggered by a hacker, which would leave your private network securely disconnected from the outside world. On your firewall computer, you can disable any unnecessary network services to protect the firewall from attack.
A packet-filtering router or circuit-level gateway type of firewall is likely suitable if your main concern is restricting outbound access from your network and your users do not need to be able to access your network remotely over the Internet. However, an application gateway is typically the best option for end users who frequently need remote access to your network.




