What is a Trojan horse?
A Trojan horse is a program that has been downloaded and installed on a computer that appears to be innocent but is in fact harmful. Unexpected changes to the computer’s settings and unexpected activity, even when it should be idle, are strong indications that a Trojan is present.
The Trojan horse typically appears as a harmless email attachment or free download. The email attachment’s hidden malware gets downloaded to the user’s device when they click on it or download the free program. Once inside, the malicious code can carry out every task the attacker gave it permission to carry out.
Trojan Infection Methods
- Phishing or other types of social engineering are used to target a user, and they may also open an infected email attachment or click a link to a malicious website.
- When a user visits a malicious website, a drive-by download of malicious software or a request to download a codec in order to play a video or audio stream may occur.
- A user visits a legitimate website that contains malicious code (such as cross-site scripting or malvertising).
- A user downloads a program whose publisher is unknown or unauthorized by organizational security policies
- Attackers exploit software vulnerabilities or gain unauthorized access to install Trojans.
Types of Trojans
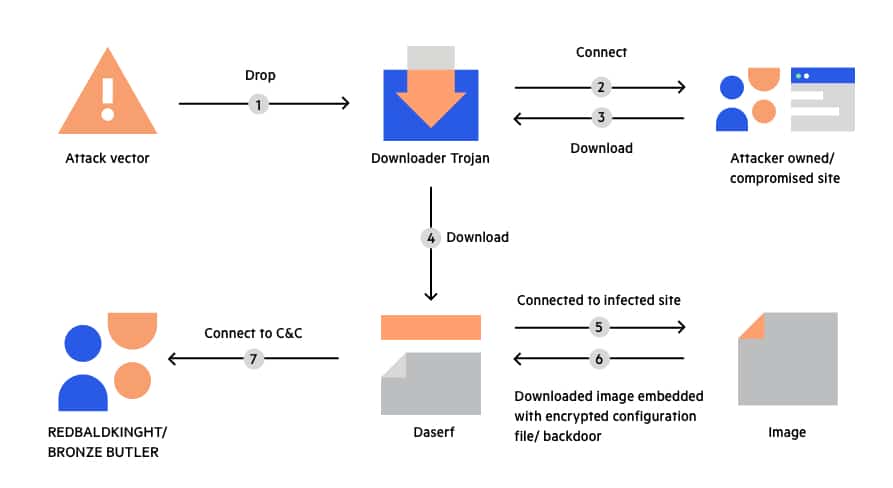
Downloader Trojan
The Emotet malware, which has since been rendered harmless but, in contrast, a backdoor Trojan, cannot execute any code on the PC itself, is one of the most well-known dropper Trojans. Instead, it spreads other malware, such as the ransomware Ryuk and the banking Trojan Trickbot.
Droppers are thus similar to downloader Trojans; however, downloaders need a network resource in order to pull malware from the network. The other harmful parts of the program package are already present in the droppers themselves. The programmers who created these sorts of Trojans have the ability to update them remotely and covertly, for instance, so that virus scanners can’t detect them with updated definitions. This method can also be used for adding new functions.
Distributed denial-of-service (DDoS) Trojan
These Trojan horses launch attacks that cause a network to become overloaded. In order to overwhelm a target web address and cause a denial of service, it will send multiple requests from one computer or from a group of computers.
Backdoor Trojan
Back door Using a backdoor, a Trojan enables an attacker to remotely enter a computer and take control of its operations. This enables the malicious actor complete control over the device, allowing them to do whatever they want, including deleting files, rebooting the computer, stealing data, or uploading malware. A network of zombie computers is regularly used to create a botnet using a backdoor Trojan.
Spyware
Spyware is a piece of software that keeps track of user activity and collects sensitive data like login passwords or banking details. They send this data back to the assailant. Generally speaking, spyware is regarded as a sort of trojan because it generally poses to be useful software.
Rootkit Trojan
Malware that conceals on a user’s computer is known as a rootkit. Its purpose is to stop dangerous programs from being detected and thus enable malware to remain active on an infected computer for a longer period of time.
Trojan Horse Malware Examples
Zeus
Zeus is a toolkit that enables hackers to build their own malware and targets financial services. To steal user passwords and financial data, the source code uses techniques like form grabbing and keystroke logging.
ILOVEYOU
This infamous Trojan was an email attachment with the subject “ILOVEYOU.” It overwrote data on the user’s computers and immediately sent itself to everyone on their contact list.
Cryptolocker
CryptoLocker, a new digital threat, first appeared. This Trojan Horse sought to hold the data captive instead of just stealing it. Ransomware is a new type of malware, and CryptoLocker was just as sinister as it sounds.
Stuxnet
A specialized Windows Trojan called Stuxnet was designed to attack Industrial Control Systems (ICS). Allegedly, it was used for an attack on Iran’s nuclear facilities. The virus modified the speed of Iranian centrifuges, making them for spin too long and too quickly and causing the equipment to be destroyed. Operator monitors continued to display business as normal.
How to Detect Trojans in Your Organization
Endpoint protection platforms
Device-based traditional antivirus, and next-generation antivirus (NGAV), may prevent zero-day and unknown trojans, and behavioral. analytics, which can spot anomalous activity on user devices, are all examples of contemporary endpoint security systems. The majority of trojans may be stopped using this set of security precautions.
Web application firewall (WAF)
By preventing the download of trojan payloads from suspicious sources, a WAF deployed at the network edge will prevent trojan infestations. Additionally, it has the ability to detect and block any unusual or suspicious network communication. When trojans “phone home” to their C&C center, WAFs can block them, rendering them ineffective, and they may help in identifying the affected systems.
Threat hunting
Threat hunting is the act of trained security analysts aggressively looking for threats on corporate networks. Systems for Security Information and Event Management (SIEM) are used by analysts to collect data using advanced searches and data analytics techniques, researchers can find evidence of trojans and other threats that are present in the local environment from hundreds of IT systems and security tools.
Triaging user complaints
A trojan can frequently be detected by a simple user complaint about a slow computer or strange user interface behavior. Behavioral analytics and data from other security tools can be used to prioritize IT support requests and identify hidden trojans.