What is an Intrusion Detection System?
A network security tool called an intrusion detection system (IDS) was originally created for detecting vulnerability exploits against specific applications or computers.
The IDS is a listen-only device as well. An administrator receives results from the IDS’s traffic monitoring. It is unable to automatically take action to prevent a detected exploit from taking control of the system.
Once within the network, attackers can quickly exploit vulnerabilities. The IDS is therefore adequate for prevention. Security information and event management require both intrusion detection and intrusion prevention systems.
How does an IDS work?
IDS operates by analyzing and monitoring various network events in order to detect incidents of malicious activity or any other kind of security violations.
It is positioned outside of your network’s real-time communication band to function as a detecting system. To check that the incoming communication is not malicious, it uses the SPAN or TAP port to analyze the copy of inline network packets.
So, if you set an IDS program, the system will be able to
- Recognize attack patterns from the network packets
- Monitor the user behavior
- Identify the abnormal traffic activity
- Ensure that user and system activity does not go against security policies

Types of IDS
Network-based, host-based, protocol-based, application protocol-based, and hybrid are the five various types of IDS.
The two most common types of IDS are
Network-based intrusion detection system (NIDS)
A whole protected network is monitored by a network IDS. Strategic locations, such as the most vulnerable subnets, are chosen across the infrastructure for its deployment. The NIDS keeps track of all network traffic flowing to and from these devices and makes decisions based on packet metadata and contents.

Host-based intrusion detection system (HIDS)
A host-based IDS monitors an eye on the computer network it is placed on. It is therefore deployed on a specific endpoint to protect it against both internal and external threats. The IDS achieves this by examining traffic, logging malicious behavior, and notifying the appropriate authorities
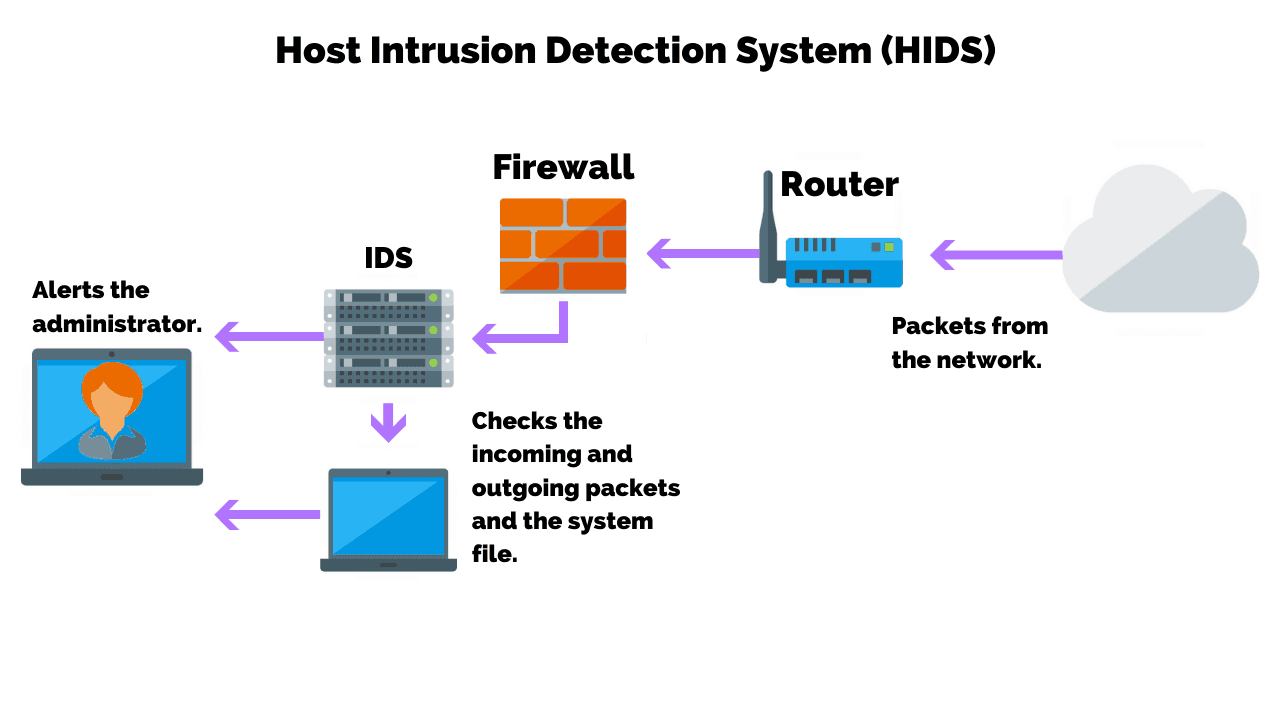
The remaining three types are as follows
Protocol-based (PIDS)
On a web server, a protocol-based intrusion detection system is usually implemented. The protocol between a user/device and the server is tracked and examined. A PIDS often sits at the server’s front end and keeps track of the protocol’s behavior and state.
Application protocol-based (APIDS)
A system or agent known as an APIDS usually sits inside the server party. It tracks and evaluates communication using application-specific protocols. For instance, while interacting with the web server, this would monitor the SQL protocol to the middleware.
Hybrid intrusion detection system
Two or more intrusion detection approaches are combined in a hybrid intrusion detection system. Using this system, system or host agent data along with network data is combined to provide a thorough understanding of the system. In terms of comparison, the hybrid intrusion detection system is more powerful. Prelude is a good example of a hybrid IDS.
Benefits of IDS
The intrusion detection system software helps in configuring rules, policies, and the appropriate actions to be taken in addition to raising alarms.
The benefits of using an IDS are listed below:
- In order to raise alarms and send notifications, it keeps monitors on routers, firewalls, key servers, and files.
- Offer centralized management for the attack correlation.
- Act as an additional layer of protection for the company.
- It analyses different attacks, identifies their patterns, and helps in organizing and implementing in place effective control.
- Give system administrators the means to identify an attack’s scope.
- A cyber security intrusion detection system help in the detection of cybersecurity problems.
Detection Method of IDS
Signature-based Method
An IDS that uses signatures monitors track of incoming network data and scans it for sequences and patterns resembling known attack signatures. It is effective for this purpose, but it cannot recognize attacks that have no known patterns.
Anomaly-based
The anomaly-based IDS is a more recent technology designed to detect unknown attacks in addition to those with established attack signatures. Instead, this form of detection uses machine learning to analyze a lot of network data and traffic.
Anomaly-based IDS employs a well-defined model of normal activity to identify abnormal behaviors. It is prone to false positives, though. For instance, a machine is labeled as an anomaly if it exhibits unusual but healthy behavior. As a result, a false alarm is raised.
Comparison of IDS with Firewalls
Both IDS and firewalls are concerned with network security, however, a firewall prevents intrusions from happening by looking outside for them, whereas an IDS monitors the network for intrusions. In order to prevent intrusion, firewalls restrict access across networks, and if an attack originates inside the network, it is undetectable. Once an intrusion has really happened, an IDS describes it and then signals an alarm.
Conclusion
Many organizations are interested in establishing secure network-based intrusion detection systems, taking into account the difficulties of ongoing system monitoring, maintenance, and alert investigation. A managed IDS solution reduces the requirement for ongoing capital expenditure by avoiding the need to hire a dedicated security person and, in some cases, by including the necessary technology.










